38: How does Identity and Access Management relate to Zero Trust?
Audio Cast:
Takeaway Points:
NIST Special Publication 800-207 is a good starting point for understanding the core concepts and design patterns
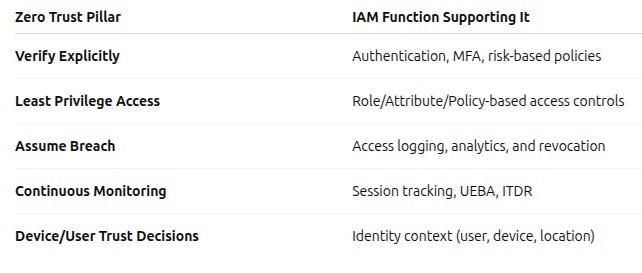
The core principles from NIST include:
No implicit trust based on network location (e.g., being inside a corporate firewall).
Continuous authentication and authorization based on dynamic risk/context.
Least privilege access is enforced per request, not per session.
Strong identity verification for users and non-human entities.
Access policies are enforced at the application, data, and service level.
Assume breach: Monitor, log, and analyze for abnormal behavior.
“Identity as the New Perimeter” sees both design and budget move from network and point security, to a focus upon information flows and identity journeys
This places greater emphasis on identity verification and validation of on-boarding data as well a focus on continuous authentication and how authorization enforcement is designed
Continuous authentication is difficult and many start on the strong authentication journey first - perhaps with native biometry and passkeys, with things like behaviour monitoring and device usage being used as a proxy for the continuous aspect
We see a need to focus upon per-request design making - so we need to have a strong approach for attribution as well as scaleable and distributed access enforcement - the typical PEP approach
To that end we see PBAC being a common concept, externalising access logic into a centrally managed model with the addition of context
Other more lightweight ideals come into play too - such as just in time access and zero standing privileges
Getting to these concepts is a strategic initiative and will require improves to access removal for existing users as well as more contextual and dynamic ways of assigning access for both standard and privileged access requests
The NIST guidelines were written before the proliferation of NHI and Agentic-AI systems were as popular as they are today
So the same principles need to be applied to more identity types - often requiring specialist tools and platforms